Hello, I am here to write my first blog and this is going to be on Cryptography which is important to understand while learning Blockchain Development.
Cryptography is used to secure transactions taking place between two nodes in a blockchain network and used to secure data from unauthorized access. There are two main concepts: hashing and cryptography where cryptography is used to encrypt messages in a P2P network and hashing is used to secure data from unauthorized access.
Terminologies related to cryptography:
Key: Some amount of information is required to get the information of the cryptographic algorithm.
Encryption: Conversion of normal text to a random sequence of bits.
Decryption: The inverse process of encryption, conversion of a Random sequence of bits to plaintext.
Cipher: The mathematical function, i.e. a cryptographic algorithm which is used to convert plaintext to ciphertext(Random sequence of bits).
Role of Cryptography in Blockchain
Blockchain is developed with a range of different cryptography concepts. The development of cryptography technology promotes restrictions for the further development of blockchain.
In the blockchain, cryptography is mainly used to protect user privacy and transaction information and ensure data consistency.
The core technologies of cryptography include symmetric encryption and asymmetric encryption.
Asymmetric cryptography uses digital signatures for verification purposes, every transaction recorded to the block is signed by the sender by digital signature and ensures that the data is not corrupted.
Cryptography plays a key role in keeping the public network secure, making it fit to maintain the integrity and security of blockchain.
Two types of cryptography are there:
Symmetric-key cryptography
Asymmetric-key cryptography
Let's discuss them;
Symmetric-key cryptography:
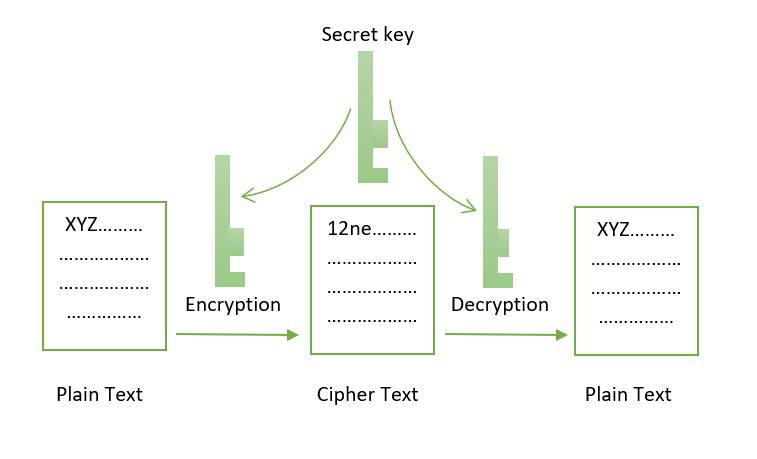
It uses a similar key for encryption as well as decryption. Also known as secret-key cryptography. The only problem is that the sender and receiver exchange keys in a secure manner. The popular symmetric-key cryptography system is Data Encryption System(DES).
Features:
It is also known as Secret key cryptography.
Both parties have the same key to keeping secrets.
It is suited for bulk encryptions.
It requires less computational power and faster transfer.
Asymmetric-key cryptography:
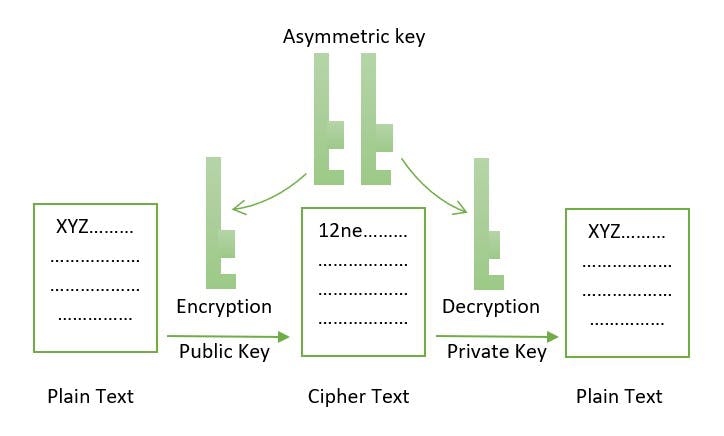
This cryptographic method uses different keys for the encryption and decryption process. This encryption method uses public and private key methods. This public key method helps completely unknown parties to share information between them like email IDs. private key helps to decrypt the messages and it also helps in the verification of the digital signature.
Features:
It is also known as Public-key cryptography.
It is often used for sharing secret keys of symmetric cryptography.
It requires a long processing time for execution.
Plays a significant role in website server authenticity.
Hash Function:
One of the most notable uses of cryptography is cryptographic hashing. Hashing enables immutability in the blockchain. The encryption in cryptographic hashing does not involve any use of keys. When a transaction is verified hash algorithm adds the hash to the block, and a new unique hash is added to the block from the original transaction. Hashing continues to combine or make new hashes, but the original footprint is still accessible. The single combined hash is called the root hash. Hash Function helps in linking the block as well as maintaining the integrity of data inside the block and any alteration in the block data leads to a break of the blockchain. Some commonly used hashed function is MD5 and SHA-1.
Properties of Cryptographic Hash:
For a particular message hash function does not change.
Every minor change in data will result in a change in a major change in the hash value.
The input value cannot be guessed from the output hash function.
They are fast and efficient as they largely rely on bitwise operations.
Benefits of Hash function in Blockchain:
Reduce the bandwidth of the transaction.
Prevent the modification in the data block.
Make verification of the transaction easier.
Benefits of Cryptography in Blockchain
There are a huge number of benefits of cryptography in blockchain some of which are stated below:
Encryption: Cryptography uses asymmetric encryption to ensure that the transaction on their network guards the information and communication against unauthorized revelation and access to information.
Immutability: This feature of cryptography makes it important for blockchain and makes it possible for blocks to get securely linked by other blocks and also to ensure the reliability of data stored in the blockchain, it also ensures that no attacker can derive a valid signature for unposed queries from previous queries and their corresponding signatures.
Security: Cryptography makes the records of transactions easier using encryption of data, and accessing of data using public and private keys. Cryptographic hashing tampering with data is not possible, making blockchain more secure.
Scalability: Cryptography makes the transaction irreversible giving the assurance that all users can rely on the accuracy of the digital ledger. It allows limitless transactions to be recorded securely in the network.
Non-repudiation: The digital signature provides the non-repudiation service to guard against any denial of a message passed by the sender. This benefit can be associated with collision resistance i.e.; since every input value has a unique hash function so there is no clash between the messages that are sent and one message can be easily differentiated from the other.
Prevent hackers: The digital signature prevents hackers from altering the data because if the data changes, the digital signature becomes invalid. With the help of cryptography, it protects the data from hackers and makes cryptography in blockchain unstoppable.
Limitations of Cryptography in Blockchain
Below are some of the limitations of cryptography in the blockchain:
Information difficult to access: Strongly encrypted and digitally signed information can be difficult to access even for a legitimate user at the most critical time of decision-making. The network can be attacked and rendered non-functional by an intruder.
High availability: It is one of the fundamental aspects of information security, and cannot be ensured through the use of cryptography. Other methods are needed to guard against the threats such as denial of service or complete breakdown of the information systems.
No protection against vulnerabilities: Cryptography does not guard against the vulnerabilities and threats that emerge from the poor design of protocols, procedures, and systems. These issues need to be fixed with the proper design of the defence infrastructure.
Expensive: Cryptography needs huge time and money investments. Public key cryptography needs the setting up and maintenance of public key infrastructure which requires huge investment. The addition of cryptographic techniques while sending messages and information processing adds to the delay.
Vulnerability: The security of cryptographic techniques depends on the complexity and difficulty of the mathematical problem. Any breakthrough in solving such mathematical problems can make cryptographic techniques vulnerable.

